In 2025, the stakes of digital risk have climbed even higher. Every business—no matter its size, sector, or location—faces smarter, faster, and often devastating cyberattacks. Therefore, securing your reputation, customer trust, and operational continuity is not just a technology issue but a growth imperative. While many organizations believe basic IT teams or off-the-shelf products can suffice, the reality quickly proves otherwise. Today, forward-looking companies across the globe rely on cybersecurity service providers or specialized cybersecurity managed service providers for robust, always-on protection.
This article explains, in detail, why these partnerships matter more than ever. Furthermore, you’ll discover how to choose the right provider, leverage real-world examples, and apply advanced yet practical cybersecurity strategies—all set within an authoritative, Yoast-optimized framework.
Why Choosing a Cybersecurity Service Provider Is Essential in 2025
Attackers adapt faster than ever before. In fact, criminals now target supply chains, remote workers, cloud assets, and even IoT devices. While headlines often spotlight breaches at giant companies, small and mid-sized businesses are increasingly in the crosshairs. Not surprisingly, cyber insurance premiums have soared, regulators levy larger fines, and customer trust evaporates after even minor incidents.
Consequently, a cybersecurity service provider becomes indispensable, offering:
- 24/7/365 vigilance—so threats are detected while you sleep.
- Scalable expertise—providing you with specialists in cloud, network, compliance, and emerging risks.
- Instant, skilled response—for rapid containment and minimal business interruption.
Because these providers are dedicated experts, they bring layered strategies, operate with tested playbooks, and maintain access to global threat intelligence. Additionally, they adapt to your evolving technology stack, regulatory landscape, and business priorities.
What a Cybersecurity Service Provider Really Does
Although each provider offers unique services, the following areas define their role in the modern digital ecosystem.
Layered, Proactive Defenses
First, cybersecurity service providers deploy advanced endpoint, network, and cloud protection. Importantly, they go beyond passive monitoring by actively hunting for threats across your environment. As a result, you receive updates and guidance—not just after an incident but continuously.
Real-Time Monitoring and Incident Response
Given the rapid pace of modern attacks, real-time threat monitoring is crucial. Whenever suspicious activity is detected, expert analysts and automated playbooks swing into action. This minimizes dwell time (the period an attacker lingers undetected) and often stops incidents before meaningful damage happens.
Managed Detection and Response (MDR)
Unlike legacy models that rely solely on traditional firewalls, MDR solutions use machine learning, behavioral analytics, and threat intelligence feeds. Furthermore, providers integrate with your systems and applications, closing visibility gaps and responding to incidents without waiting for internal escalation.
Vulnerability Management and Patch Automation
Because most breaches exploit known, unpatched vulnerabilities, service providers continuously scan for weaknesses. As new exploits surface, they prioritize remediation and even automate critical patching—lowering your exposure dramatically.
Compliance and Regulation Support
Staying compliant is more complicated each year. Nevertheless, cybersecurity service providers automate compliance evidence collection, prepare you for audits, and generate reports for GDPR, HIPAA, PCI DSS, CCPA, ISO 27001, SOC 2, and new regulations.
Security Awareness and Cultural Resilience
People remain the biggest risk factor. Consequently, a leading provider will train your staff—via phishing simulations, microlearning, and customized policies—fostering a culture of security as part of daily operations.
How Managed Service Providers (MSSPs) Maximize Cyber Defense
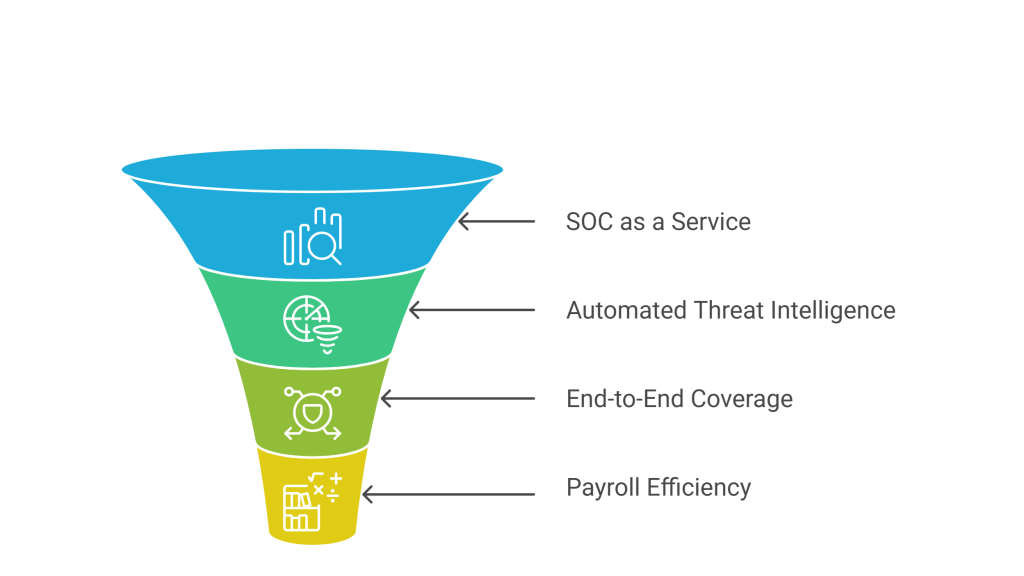
While classic service providers deliver assessments and short-term projects, MSSPs act as an extension of your team. They manage and evolve your entire security posture, using both technological innovation and human expertise.
Security Operations Center (SOC) as a Service
Your MSSP operates a state-of-the-art SOC, staffed with analysts, threat hunters, and incident responders. Importantly, many SOCs blend human insight with AI, so even stealthy or novel attacks are detected.
Automated Threat Intelligence
Truly advanced MSSPs use live threat feeds—gathered from global sources, law enforcement, and dark web monitoring—enabling you to block attacks that haven’t even hit the headlines.
End-to-End Coverage
MSSPs cover every layer: endpoints, cloud, networks, APIs, vendors, and even physical assets. Because they integrate with your business apps, they spot cross-channel threats and enforce unified policies.
Payroll Efficiency and Cost Control
By outsourcing, you access world-class security without hiring, retaining, and upskilling expensive internal staff. Furthermore, costs are predictable—using flat rates or tiered packages—while value delivered is measurable: incidents averted, response times shrunk, and regulatory fines avoided.
Enterprise Projects: When and Where to Use a Cybersecurity Service Provider
Organizations use cybersecurity service providers for more than just “firefighting.” Here are high-value, ongoing, and project-based scenarios:
1. Cloud Transformation & Hybrid Migration
As you move workloads to AWS, Azure, or Google Cloud, a managed provider maps protection across both traditional and cloud systems, securing data flow, access, and compliance simultaneously.
2. Regulatory or Client-Driven Security Certification
When clients demand ISO27001/SOC 2/PCI compliance, providers build and manage controls, automate documentation, and perform gap analysis until you pass the audit.
3. New App or Website Launch
Whenever a business launches a FinTech platform, eCommerce store, or mobile app, cybersecurity partners enable “secure by design” launches, reviewing code, stress-testing APIs, and showing leadership during public bug bounty phases.
4. M&A, Joint Venture, and Supply Chain Expansion
Mergers or multi-partner projects create new points of vulnerability. Providers assess inherited risk, implement segmentation, and orchestrate secure, collaborative environments.
5. IoT, Smart Devices, and Edge Rollouts
As more sensors, controls, and devices are connected, MSSPs deliver segmentation, secure onboarding, continuous monitoring, and anomaly detection at scale.
Business Benefits: 10 Ways Providers Enhance Your Organization
1. Reduced Dwell Time
Since response is instant, attackers can’t linger in your environment—minimizing risk, damage, and loss.
2. Workforce Empowerment
Through user-friendly simulators and training, your employees become security sentinels instead of liability points.
3. Strategic Risk Alignment
Providers tailor defenses to the true risk profile of your organization, not just generic templates.
4. Innovation & Growth Acceleration
Knowing protection is robust, businesses confidently launch new products, enter new markets, and adopt new technologies.
5. Reputation and Brand Value
Demonstrating a proactive, always-on security posture reassures both customers and investors, enabling growth.
6. Disaster Recovery and Business Continuity
Providers establish, test, and maintain cyber-resilient recovery plans, so ransomware or breaches don’t cripple you.
7. Peace of Mind
Executives sleep better, teams waste less energy on fear, and focus returns to your core mission.
8. Regulatory Confidence
Automated evidence lowers audit stress, while avoiding fines or lost contracts.
9. Reduced Downtime
Automated detection, strong backups, and skilled incident response reduce or eliminate costly downtime.
10. Forecastable Security Budgets
Flat-rate, scalable packages let you plan and invest smartly—even as your organization grows.
Real-World Success Story
In 2024, a regional healthcare provider suffered a ransomware attack that encrypted clinical records. With only basic anti-virus in place, the team lost days of operations, faced media scrutiny, and nearly $1M in compliance penalties. After hiring a managed security service provider, the organization implemented 24/7 detection, regular vulnerability patching, encrypted backups, simulated phishing, and real-time risk scoring. When another attack was attempted in late 2025, it was stopped before it could affect a single patient record or device. Regulators praised their turnaround, patients returned, and cyber insurance premiums dropped by 40%.
How to Select the Best Cybersecurity Service Provider
The right partner is critical; here’s how to choose wisely:
1. Clarify Your Needs
Assess your company’s compliance obligations, sensitive data flows, network/app complexity, and pain points. Match these to providers’ listed competencies. For example, financial firms need deep PCI and anti-fraud work, while SaaS companies must prioritize app and cloud security.
2. Review Provider Credentials
- Look for ISO 27001, SOC 2, PCI DSS certifications.
- Ask for reference projects in your vertical.
- Study NPS (Net Promoter Score), review sites, and analyst rankings.
3. Evaluate Service Level Agreements
Demand detailed SLAs specifying response times, containment metrics, communication protocols, and breach-support guarantees.
4. Examine the Technology Stack
Confirm inclusion of NextGen Firewalls (NGFW), EDR/XDR, SIEM integration, threat feeds, application security, and vulnerability management.
5. Require Customization and Communication
Insist on tailored security roadmaps, regular reporting, direct lines to decision-makers, and proven training programs for your staff.
Future Trends: Where Cybersecurity Service Providers Are Headed
AI-Driven Predictive Security
Providers use AI to predict attack vectors, simulate threats, and automate detection/response—outpacing human attackers.
Zero Trust Everywhere
Trust no device, user, or application by default. Every access is verified—internally, externally, and across hybrid environments.
Integration Beyond the Enterprise
Providers now include vendor, customer, and supply chain risk within their continuous monitoring—extending protection beyond the company edge.
Digital Privacy and Ethical Security
Data protection laws accelerate. Providers help create, review, and maintain ethical, privacy-focused security policies.
Best Practices for Collaborating With Your Cybersecurity Service Provider
- Hold regular risk reviews and policy updates.
- Share upcoming business or technology changes proactively.
- Encourage staff security champions; make reporting issues easy and rewarding.
- Run “red team/blue team” simulations together to stress-test defenses.
- Insist on continual improvement, not just “install and walk away” service.
Conclusion: Strengthen, Simplify, Succeed
In 2025, a cybersecurity service provider is more than an outsourced vendor—they are an engine for safety, innovation, and brand trust. With cyber risks surging, only those who invest in professional, 24/7, multilayered defense can guarantee the continuity, compliance, and growth their stakeholders expect.
Therefore, whether you’re scaling, modernizing, or safeguarding your current assets, the choice is clear: Partner with a cybersecurity service provider and future-proof both your technology and your reputation.
Frequently Asked Questions
What does a cybersecurity service provider do that IT cannot?
Unlike general IT, cybersecurity providers focus exclusively on emerging threats, advanced defense, legal compliance, and instant response 24/7. They deliver expertise, coverage, and reliability most IT shops can’t afford to build internally.
Do only big companies need a managed provider?
No. While large firms have huge risk, small and medium businesses are increasingly targeted and, often, less equipped for defense. Providers tailor packages to your size and industry so you receive enterprise-level protection at accessible rates.
What’s included in a typical service provider contract?
Typically: 24/7 threat monitoring and response, compliance support, tool deployment and management, ongoing risk assessments, reporting, periodic training, and incident management support.
Will the provider work with our in-house team?
Absolutely. Best-in-class providers augment and enable your internal IT/security staff, handle escalation, and co-manage security roadmaps.
How are results measured?
Your dashboard should show detected/block threats, response times, downtime prevented, and compliance scores—offering full transparency.

