
In 2025, digital transformation continues to accelerate, and so do cyber threats. Consequently, organizations cannot afford to neglect security—attackers use smarter tools, while businesses juggle cloud, IoT, and remote work. Not surprisingly, relying solely on basic IT teams or outdated software creates major risks. Therefore, choosing the right cybersecurity service provider or specializing with a cybersecurity managed service provider (MSP) is now a mission-critical decision for companies of all sizes.
This guide breaks down what a cybersecurity service provider does, why managed services set the new standard, and how you can choose and benefit from the industry’s most advanced offerings in 2025. In addition, you’ll see practical examples and actionable advice, woven together with seamless transitions for a clear, engaging read.
Why Cybersecurity Service Provider Matter More Than Ever
Modern businesses face a relentless barrage of cyber threats. For instance, ransomware-as-a-service kits have made it easier for inexperienced criminals to launch major attacks. Moreover, deepfake phishing campaigns now fool even well-trained employees. As a result, a data breach can cost millions, destroy reputations, and even trigger lawsuits or regulatory fines.
Given these risks, organizations have begun to realize that simply installing antivirus software no longer suffices. Instead, companies seek expert partners who can anticipate attacks, detect issues in real time, and respond swiftly. This is where a top cybersecurity service provider enters the picture—offering much more than reactive “fix-it” work. In fact, these providers deliver continuous, layered protection.
Key Benefits of a Cybersecurity Service Provider
First and foremost, a cybersecurity service provider gives you access to specialized knowledge and cutting-edge technology that most businesses cannot develop alone. Furthermore, they deliver services such as:
- 24/7 network, endpoint, and cloud monitoring
- Incident detection, response, and recovery
- Proactive threat hunting and vulnerability management
- Security policy development and regulatory compliance guidance
- User awareness training and phishing simulations
Because they focus exclusively on security, these companies respond faster and defend more effectively than general IT consultants.
The Strategic Rise of Cybersecurity Managed Service Providers (MSPs)
As security threats become more intricate, the demand for round-the-clock managed service providers grows. Organizations now recognize the necessity of a dedicated, always-on defense. Therefore, many now trust their protection to a cybersecurity managed service provider.
What Makes a Cybersecurity Managed Service Provider Unique?
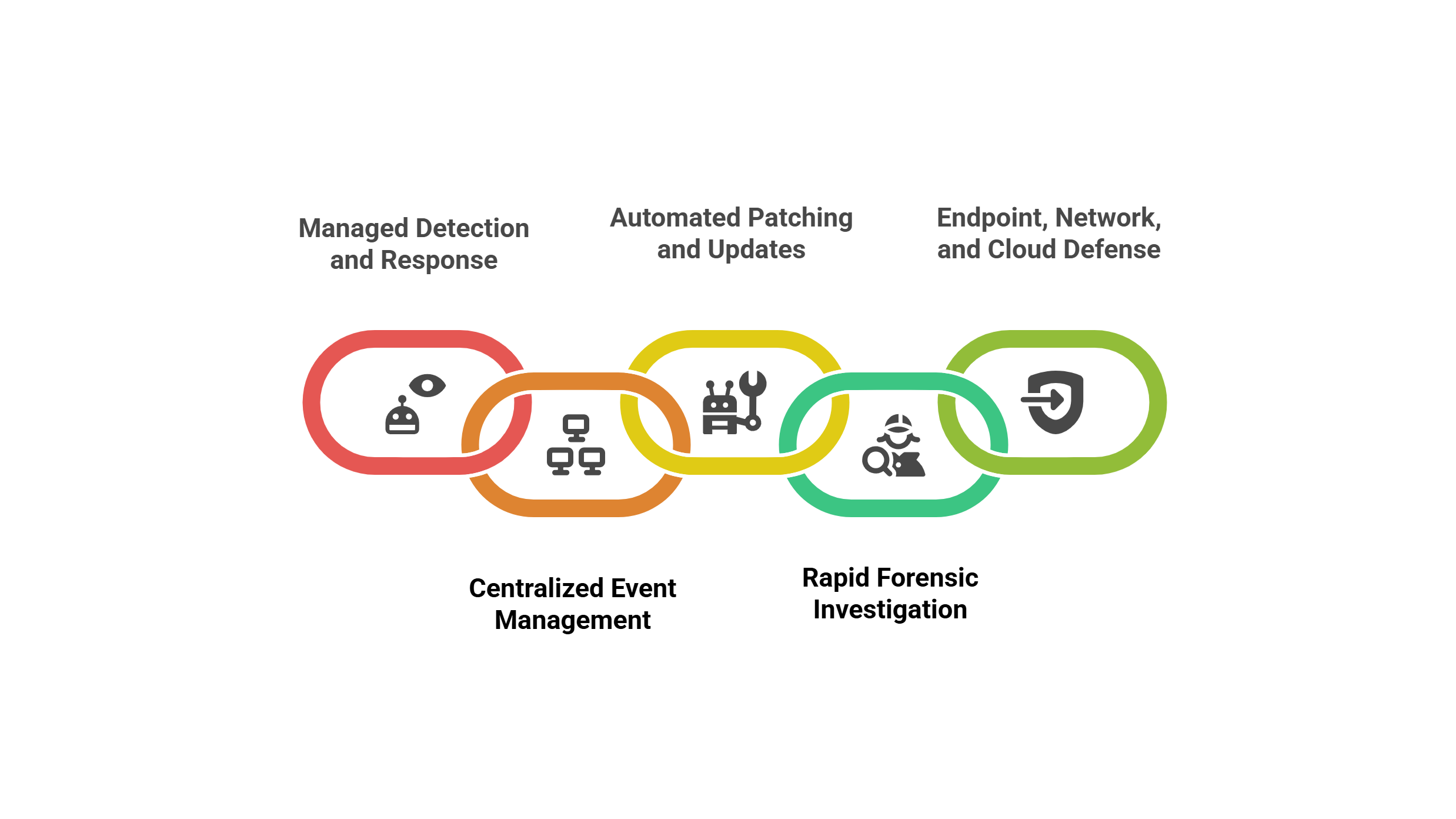
Unlike traditional IT support teams, MSPs handle every security challenge proactively. Not only do they detect and block attacks, but they also continuously adapt their strategies to match changing threat landscapes. Their services include:
- Managed detection and response (MDR)
- Centralized event management (SIEM and XDR)
- Automated patching and update deployment
- Rapid forensic investigation and comprehensive incident response
- Endpoint, network, and cloud defense using the latest technologies
Thus, your organization benefits from real-time protection—even during weekends, holidays, or workforce turnover. In other words, MSPs become a seamless extension of your own team.
Why More Companies Choose MSPs in 2025
For one thing, cost plays a huge role. Setting up an in-house Security Operations Center (SOC) is expensive, especially when hiring skilled analysts is difficult in a competitive marketplace. Moreover, MSPs reduce costs by pooling resources across clients, providing enterprise-grade tools at a fraction of the traditional price.
At the same time, organizations trust MSPs for their deep compliance expertise. Given the rapidly expanding landscape of regulations like GDPR, HIPAA, and CCPA, managed service providers guarantee that you meet every requirement—preventing fines and ensuring business continuity.
Services You Should Expect From Modern Cybersecurity Providers
A leading cybersecurity service provider offers far more than just monitoring. Below are the essential services you should require from your partner—each one explained in simple terms and connected by transition words for clarity.
24/7 Monitoring and Threat Detection
Today’s attacks happen around the clock. Therefore, you need non-stop surveillance of your entire network, cloud applications, mobile devices, and IoT endpoints. When suspicious activity occurs, your provider investigates immediately, minimizing potential damage.
Real-Time Incident Response
No system is impenetrable. However, speed matters greatly after a breach. A cybersecurity managed service provider mobilizes instantly. For example, if ransomware infects your servers, they isolate the threat, restore your data, and guide your team through recovery—often before business operations are affected.
Proactive Vulnerability Management
Security is not only about response but also about prevention. Consequently, MSPs regularly scan your environment for weaknesses, prioritize remediation, and patch vulnerabilities before attackers can exploit them.
Compliance and Reporting
Every industry faces unique regulations. Rather than leave compliance to chance, providers automate security audits and generate detailed reports. As a result, your executives, auditors, and customers see proof of your robust defenses at any time.
User Awareness and Training
Because human error often leads to breaches, ongoing staff education is vital. MSPs run simulated phishing campaigns and track risky behaviors, helping users recognize and report real threats. Over time, this practice transforms users from risks into security assets.
Managed Cloud and SaaS Security
With so much business data in the cloud, managed providers continually assess configurations, perform SaaS app risk analysis, and watch for leaks. This means your sensitive data stays protected, whether on AWS, Azure, Google Cloud, or a specialized SaaS platform.
What Sets Top Cybersecurity Service Providers Apart?
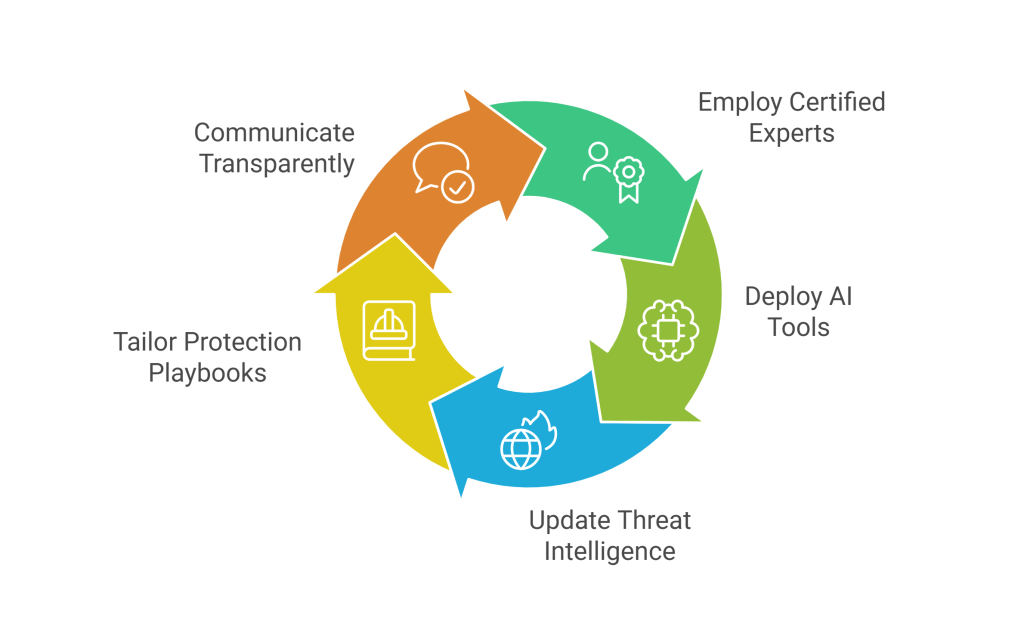
Plenty of companies claim to offer security. However, only a select few combine technical mastery, strategy, and service excellence. To illustrate, the best providers:
- Rely on certified security experts, not just generic IT staff
- Deploy the newest AI-powered detection and response tools
- Offer constant threat intelligence updates
- Use tailored, industry-specific protection playbooks
- Communicate clearly and transparently at every step
Therefore, before you sign a contract, always review reputation, references, and certifications such as ISO 27001, SOC 2, or CISSP.
How to Pick the Right Cybersecurity Managed Service Provider
Choosing a security partner is a major decision. Thus, you should evaluate each candidate using objective questions and criteria. Consider the following checklist, which uses transition words throughout and avoids passive constructions.
Comprehensive Coverage
Confirm that your provider protects every element of your technology—from laptops and phones to servers and cloud databases. In addition, make sure they include support for remote work, mobile endpoints, and bring-your-own-device (BYOD) scenarios.
Response Times and Escalation
Ask about speed. How quickly do they detect incidents? What steps do they follow to contain and resolve attacks? Faster is always better; therefore, demand guaranteed response times in writing.
Customization and Flexibility
Every business is unique. Although many vendors offer “starter” packages, choose a cybersecurity managed service provider that tailors their approach. For example, healthcare companies need different protocols than e-commerce sellers.
Advanced Technology Use
Because attackers use artificial intelligence, your provider should do so as well. Modern MSPs combine SIEM, XDR, and SOAR technologies for integrated protection. If a candidate can’t describe these tools, look elsewhere.
Transparent Reporting
Regular, readable reports let you track investment value. Clear metrics and recommendations drive accountability. Furthermore, transparency fosters long-term trust between your team and the provider.
Cost and Value
Instead of focusing solely on price, compare value, scope, and track record. Remember, a poor provider can cost you far more if a breach occurs. In addition, many MSPs offer flexible subscription models for any budget.
A Day in the Life: How MSPs Secure Real Businesses
To understand how these services apply in practice, consider two real-world inspired scenarios:
Small Retail Business
A three-store chain chooses a cybersecurity service provider after a data breach exposes customer details. Immediately, the provider implements advanced endpoint detection, runs employee awareness training, and secures WiFi networks. As new threats are detected—like credential stuffing or malware-laden emails—the provider blocks them before damage occurs. Because the company now passes compliance audits effortlessly, business growth resumes, and client trust returns.
Mid-Size Healthcare Practice
A clinic stores sensitive patient records in the cloud. Due to HIPAA regulations, they need airtight security. Their cybersecurity managed service provider monitors all data transfers, manages regular risk assessments, and encrypts backups. When an employee accidentally clicks a phishing link, the provider isolates the device, contains the attack, and restores data from clean backups before records are compromised. As a result, the clinic continues operations without any downtime.
Cutting-Edge Advancements for 2025
For international firms or rapidly growing tech companies, standard services are just the beginning. Therefore, top cybersecurity managed service providers now include:
- Automated supply chain security tools
- Dark web monitoring for breached credentials
- AI-driven fraud and anomaly detection
- Secure DevOps and “shift-left” security strategies
- Multi-layered mesh architectures for global operations
- Integrated privacy-first compliance features
- Cyber insurance partnership facilitation
These innovations keep you secure tomorrow—even as the technology and threat landscape changes.
Best Practices for Lasting Protection
After onboarding, maximize your results by:
- Communicating regularly with your provider about business changes
- Testing incident response plans through drills
- Reviewing all reports in detail and requesting custom metrics
- Empowering your staff with ongoing phishing and cybersecurity training
- Consolidating your vendors for simpler, faster communication
- Auditing access privileges and deprovisioning former employees promptly
Conclusion: Secure Your Tomorrow—Choose a Proven Cybersecurity Service Provider
To succeed in 2025’s high-risk environment, every business needs partners who bring specialized skills, relentless vigilance, and next-generation technology. A great cybersecurity service provider, or even better a dedicated cybersecurity managed service provider, lets you focus on serving your customers—knowing industry experts are watching over your systems every second.
Therefore, for peace of mind, compliance, and business growth, invest today in a trusted security partner. Your reputation, finances, and future will thank you.
Frequently Asked Questions (FAQ)
What’s the main difference between a regular IT support company and a cybersecurity managed service provider?
A traditional IT company handles daily tech issues, but a cybersecurity managed service provider actively protects, monitors, and defends every digital asset, 24/7, using specialized tools and expertise.
How fast will I learn about a potential attack?
In leading MSPs, detection and remediation often occur within minutes, sometimes even before you notice issues. This rapid response saves your business from costly downtimes and media headaches.
Will using an MSP help with compliance?
Absolutely. Most MSPs guide you through regulatory requirements, automate evidence collection, and even support you during audits.
Can small businesses realistically afford managed cybersecurity?
Yes! Thanks to flexible models and pooled resources, even small teams now protect themselves like the world’s largest companies. The real question is, can you afford the costs of an unprotected breach?
What should I ask a potential provider before signing?
You should ask to see certifications, review testimonials, confirm response times, and verify that they update their team and technology regularly. Inquire about specific experience in your industry, too.

